When you buy a small or mid-sized business (SMB), you're also inheriting its cybersecurity risks - and the stakes are high. 43% of cyberattacks target small businesses, and the average data breach costs $3.31 million. Weak security can lead to data theft, ransomware, or even destroy the value of your investment.
Here’s what you need to know:
- Hidden risks like outdated systems, unused accounts, and weak access controls are common.
- Attackers act fast - they can exploit vulnerabilities within 24 hours and move through networks in 62 minutes.
- Prioritize fixes by risk level: high-risk issues (e.g., exposed RDP ports) need immediate attention, while medium and low risks can follow a timeline.
- Employee training matters - 68% of breaches involve human error.
This checklist helps you identify and assess the IT infrastructure during due diligence and after closing the deal. From network security to employee practices, it’s a step-by-step guide to protect your investment.
Key Tips:
- Use Multi-Factor Authentication (MFA) to reduce account compromises by 99.9%.
- Replace outdated hardware/software and secure all devices with encryption and remote wipe capabilities.
- Audit third-party integrations quarterly to limit unnecessary access.
- Test backups regularly - cloud sync tools like Dropbox aren’t true backups.
Cybersecurity isn’t just technical; it’s about preparation and vigilance. Follow this guide to safeguard your acquisition from day one.
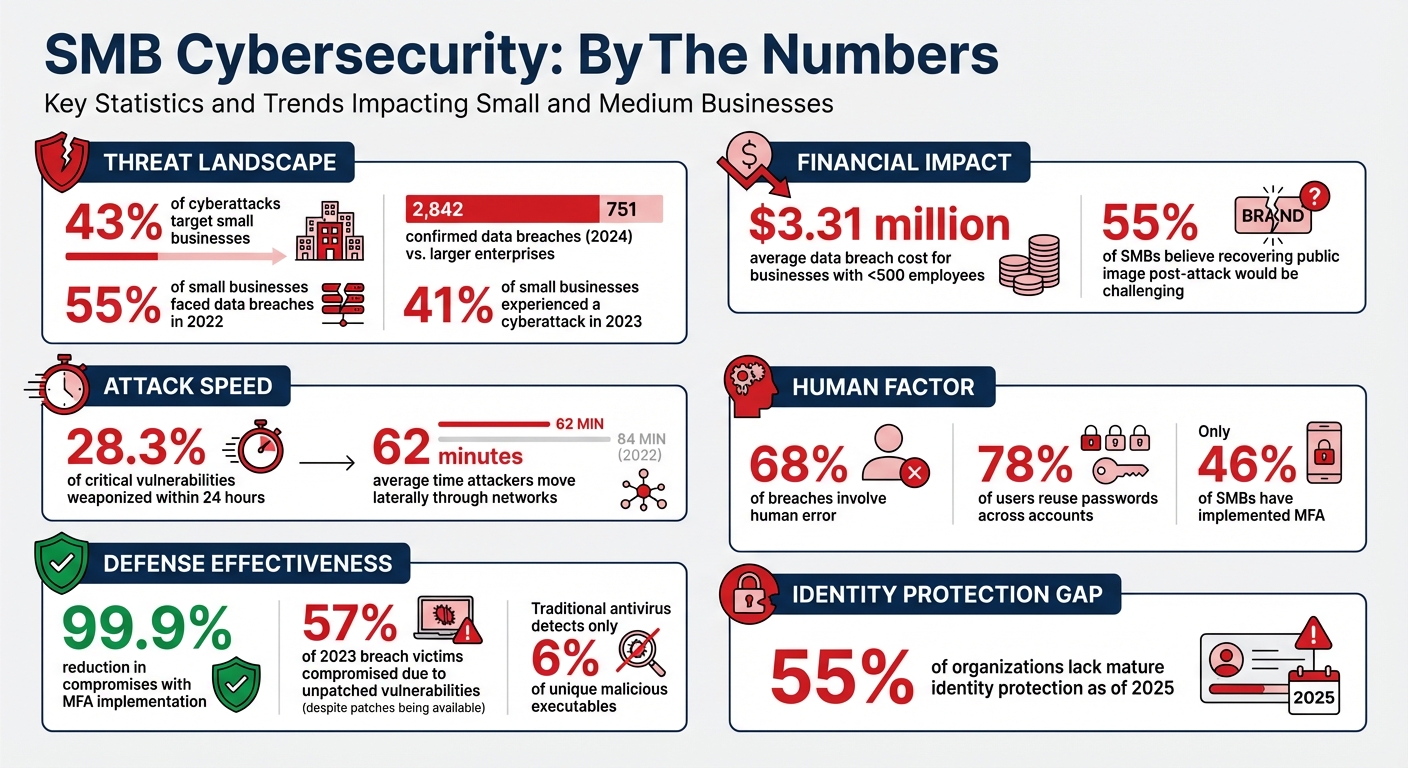
SMB Cybersecurity Statistics: Attack Frequency, Costs, and Defense Effectiveness
Assess your SMB cybersecurity defences at warp-speed
sbb-itb-a3ef7c1
Network Security Assessment
When it comes to mergers and acquisitions, your network is one of the most vulnerable entry points for potential attacks. To safeguard it, start with a thorough device inventory, evaluate your network's configuration, and carefully examine third-party access points.
Hardware and Connected Device Inventory
Begin by cataloging every device connected to your network - this includes laptops, desktops, mobile phones, tablets, servers, routers, switches, printers, and IoT devices. Be on the lookout for unmanaged devices, often called "shadow assets", as these can significantly increase your exposure to risks.
Automated tools can make this process faster and more efficient. For instance, the Cybersecurity and Infrastructure Security Agency (CISA) provides free vulnerability scanning services, while tools like Malcolm can automatically detect connected devices on your network. Alongside automated scans, conduct a physical audit of all locations to uncover hidden or overlooked hardware. As Teal Tech highlights:
Older software and hardware are more vulnerable to security breaches than newer stuff. A typical setup is an old desktop PC running Windows XP... solely to run a printer.
If you encounter outdated systems like this, don’t just document them - replace them immediately.
For each device, assign a risk score: High (devices exposed to the internet or handling sensitive data), Medium (devices used internally with some exposure), or Low (isolated devices with minimal risk). Additionally, ensure all mobile devices and laptops have remote wipe capabilities enabled to protect data in case of loss or theft.
Network Configuration and Firewall Review
After identifying all devices, shift your focus to how your network is configured and protected. Start with your firewall rules, paying particular attention to exposed RDP ports. These should be secured behind a VPN and protected with multi-factor authentication (MFA). Replace all default router passwords, and confirm that your Wi-Fi networks use WPA3 encryption. Guest networks should be completely isolated from your primary business network.
Take steps to prevent email spoofing by verifying your SPF records through DNS lookup. Additionally, ensure that group policy settings are configured to lock out accounts after a set number of failed login attempts, reducing the risk of brute-force attacks. Don’t forget to physically inspect your infrastructure - servers, routers, and switches should be housed in secure, locked rooms rather than left in open, easily accessible areas.
Vendor and Third-Party Integration Checks
Once your internal network is secure, turn your attention to external integrations. Audit all SaaS tools, cloud platforms, and third-party connections to eliminate inactive accounts and enforce the principle of least privilege. This means each tool or integration should only have the permissions it needs to function, rather than unrestricted admin access.
Make it a habit to run quarterly audits to identify and remove unused integrations or API-level access from platforms like Zapier or Microsoft 365. Even one forgotten vendor login can serve as a weak link for attackers. Document who has access, the level of permissions they have, and when those permissions were last reviewed to maintain control over your network’s external connections.
Software Security and Update Management
Once you've hardened your network, securing software systems and keeping them updated becomes essential to fend off potential exploits. Software vulnerabilities are a growing concern for SMBs, with 57% of breach victims in 2023 being compromised due to an unpatched, known vulnerability - despite patches being available. Alarmingly, 28.3% of critical vulnerabilities are weaponized within 24 hours of their disclosure. As Dana Larson, Sr. Product Marketing Manager at CrowdStrike, aptly states:
Patch management is the cornerstone of your vulnerability management plan.
Patch Management and Update Policies
Begin by inventorying all software assets, including operating systems, business applications, cloud platforms like Microsoft 365 or Google Workspace, and even browser extensions. Pay particular attention to legacy systems running unsupported software, such as Windows 7 or outdated QuickBooks versions. These outdated systems no longer receive security patches and should be replaced immediately.
Adopt a risk-based prioritization framework for patching. Regularly consult resources like CISA's Known Exploited Vulnerabilities (KEV) Catalog to identify actively exploited flaws. Whenever possible, configure systems to automatically install security updates. For critical systems that require manual updates, create a documented schedule and assign responsibility to ensure patches are applied within days, not weeks.
Once your software updates are under control, focus on securing endpoints to combat active threats.
Endpoint Security and Malware Prevention
Traditional antivirus solutions fall short, detecting only 6% of unique malicious executables. To address this gap, deploy EDR (Endpoint Detection and Response) or MDR (Managed Detection and Response) solutions, which use behavior-based detection and offer 24/7 threat monitoring. In 2023, the average "breakout time" - the time attackers take to move from the initial compromise to other systems - dropped to just 62 minutes, making automated threat isolation tools indispensable.
To protect sensitive data, encrypt all laptops and mobile devices using tools like Windows BitLocker. Disable unused ports and services on endpoints to minimize your attack surface, and implement application allowlisting to ensure only approved software runs on company devices. Additionally, isolate sensitive systems, such as those used for payment processing, from devices used for general web browsing.
Cloud Application and SaaS Security
A common misconception among SMBs is that cloud synchronization services like Dropbox or OneDrive serve as backups. They don’t. Here’s why:
If ransomware encrypts a file and that file syncs, the encrypted version overwrites everything.
Ensure your cloud applications provide true versioned backups instead of basic file synchronization. Use free tools like CISA's Secure Cloud Business Applications (SCuBA) to evaluate and strengthen the configurations of SaaS platforms, focusing on MFA and audit logging. Conduct quarterly audits to remove unused SaaS integrations and deactivate former contractor accounts from admin panels. For automation tools like Zapier, review API-level permissions and enforce the principle of least privilege.
Multi-factor authentication (MFA) is a game-changer, reducing compromises by 99.9% when implemented. Make MFA mandatory for all cloud application admin panels and user accounts.
These software security measures work hand-in-hand with your broader cybersecurity strategy, fortifying every layer of your IT infrastructure.
Access Control and Authentication
After addressing software and endpoint security, it's crucial to limit system access to reduce the risks of credential-based attacks. Why? Because as of 2025, 55% of organizations still lack mature identity protection, and smaller businesses with fewer than 1,000 employees faced 2,842 confirmed data breaches in 2024 - nearly four times the number experienced by larger enterprises. Attackers are increasingly targeting weak passwords and lax access controls, using them to move through networks undetected. Strengthening identity controls is a key step to bolster your defenses.
Multi-Factor Authentication (MFA) and Password Policies
Start by requiring MFA for all critical accounts. It’s a simple yet powerful measure - organizations using MFA see 99.9% fewer compromises, but only 46% of small and medium businesses (SMBs) have implemented it.
Not all MFA methods offer the same level of security. Basic SMS codes are vulnerable to SIM-swapping attacks, and repeated push notifications can lead to "MFA fatigue", where users accidentally approve malicious requests. To counter these risks, consider switching to number matching or FIDO-based hardware keys, which provide stronger protection against phishing attempts.
For password management, a password manager can help tackle the issue of password reuse - an alarming 78% of users reuse passwords across multiple accounts. Additionally, set up group policies to lock accounts automatically after a certain number of failed login attempts. This simple step can thwart brute-force attacks.
Role-Based Access Controls (RBAC)
Adopt the principle of least privilege by granting employees access only to the data and applications necessary for their roles. Group employees into security categories with shared permissions to streamline management and auditing processes.
It’s equally important to regularly review administrative privileges. Keep a documented record of why each admin account exists and avoid shared credentials like "admin@" or "billing@" to improve accountability and reduce risks.
Inactive accounts are another weak point. Conduct quarterly access reviews to disable accounts of former employees. Hackers often exploit these accounts, using information from social platforms like LinkedIn to identify potential targets.
Vendor Access and Remote Login Security
Securing internal access is only part of the equation - you also need to lock down external entry points. If your team uses Remote Desktop Protocol (RDP), never leave it exposed to the internet. Instead, protect it with a VPN that uses MFA or switch to Zero Trust Network Access (ZTNA).
Third-party integrations and SaaS applications also deserve scrutiny. Perform quarterly audits to identify and remove unused permissions or accounts belonging to former contractors. For automation tools like Zapier, ensure their API-level access is limited to only what’s necessary, such as read-only permissions.
Finally, for employees using personal devices for work, implement Mobile Device Management (MDM). This allows you to enforce encryption and remotely wipe sensitive data if needed.
Data Protection and Compliance
After securing access controls, the next priority is safeguarding the data itself. Here's why: in 2022, 55% of small businesses faced data breaches, with the average cost for businesses with fewer than 500 employees surpassing $3.31 million. Beyond financial losses, 55% of SMBs believe recovering their public image after a cyberattack would be a significant challenge. This makes strong encryption, dependable backups, and strict compliance measures not just important - but absolutely necessary to survive in today's digital landscape.
Data Encryption and Backup Policies
Start by enabling full-disk encryption on all laptops and desktops. For instance, Windows 10/11 Pro offers BitLocker, which can be set up in just a few minutes. Safeguard your recovery keys securely - this ensures that even if hardware is lost or stolen, the data remains inaccessible to unauthorized users.
When it comes to backups, follow the 3-2-1 rule: keep three copies of your data, use two different storage types, and store one copy off-site. Keep in mind that cloud synchronization tools like Dropbox or OneDrive aren't true backup solutions. These tools mirror changes - including deletions or ransomware encryptions - in real time. Real backups should be isolated, versioned, and encrypted.
"If you've never restored a file, you're assuming recovery works. That's not a strategy, it's a risk by default."
– CitySource Solutions
Test your backups at least once every quarter by performing a full restore. This ensures you can recover data when it matters most. Also, define two critical metrics for your business: your Recovery Time Objective (RTO), which is the maximum acceptable downtime, and your Recovery Point Objective (RPO), which specifies how much data loss your business can tolerate.
Once encryption and backups are in place, ensure that these processes align with the necessary regulatory standards.
Compliance with Regulations (HIPAA, PCI-DSS, etc.)
After implementing encryption and backup protocols, verify that your operations meet all relevant legal and industry standards. Businesses handling sensitive data - such as health records or payment card information - must comply with regulations like HIPAA, PCI-DSS, or GDPR.
Compliance isn't just about avoiding fines; it can also set you apart. Demonstrating a commitment to regulatory standards can make SMBs more appealing to enterprise clients. To maintain compliance, review user permissions regularly to ensure role-based access, enable multi-factor authentication on all accounts, and encrypt backup data to prevent unauthorized access. Conduct these reviews quarterly to stay ahead of potential risks.
Incident Response and Recovery Plans
Even with robust defenses, cyberattacks remain a possibility. In 2023, 41% of small businesses experienced a cyberattack, with attackers now able to move laterally within networks in just 62 minutes - down from 84 minutes in 2022. This makes having a well-prepared incident response plan non-negotiable.
Your Incident Response Plan (IRP) should clearly define roles and responsibilities. Identify who will coordinate the response, handle technical fixes, and manage communications both internally and externally. Include detailed playbooks for specific scenarios - like phishing attacks, ransomware, or data breaches - and outline immediate containment steps, such as isolating compromised devices or accounts.
"In the event of a successful attack, having a plan in place will help you act quickly and efficiently to involve the right people, take the necessary actions and mitigate the damage."
– Dana Larson, Sr. Product Marketing Manager, CrowdStrike
Regularly run tabletop exercises to ensure your team knows how to respond under pressure. Additionally, pre-vet external partners - such as IT consultants, legal advisors, and public relations experts - so they're ready to assist when needed. After any incident, review the response to identify areas for improvement and update your plan accordingly.
"Cybersecurity is about culture as much as it is about technology. Culture cannot be delegated."
– CISA
Human Factors and Employee Training
No matter how advanced your technical defenses are, they won’t stand a chance against human error. In fact, 68% of all security breaches stem from mistakes made by people. With 43% of cyberattacks now targeting small businesses, employees can either strengthen your defenses or leave you wide open to threats. The key difference? Proper training, awareness, and clear operational guidelines.
Phishing and Social Engineering Awareness
Small businesses experienced a staggering 2,842 confirmed data breaches in a recent period - nearly quadruple the 751 breaches reported by larger companies. Most of these attacks began with a single, seemingly innocent action: an employee clicking a malicious link or responding to a fraudulent request.
To combat this, training should focus on the essentials: spotting fake login pages, identifying spoofed invoices, recognizing suspicious email attachments, and staying ahead of newer tactics like QR code scams. Attackers often rely on psychological manipulation - using urgency or authority to trick employees into approving wire transfers or sharing sensitive data.
"If you don't measure human behavior in your security program, you won't see the gap until it's too late."
– CitySource Solutions
Regular simulated phishing tests are a game changer. By sending fake phishing emails, you can identify employees who fall for them and provide immediate, hands-on training. This approach is far more effective than annual training sessions because it builds practical, real-world instincts. Additionally, implement a formal verification process for sensitive requests, such as requiring a phone call to confirm emailed instructions involving money or data.
Some employees, like those in Finance, HR, and Executive roles, are especially high-risk. These groups handle the most sensitive information and are often targeted by sophisticated scams like Business Email Compromise (BEC). They need tailored training to recognize and defend against these threats.
Device Security and BYOD Policies
Employee awareness is just one piece of the puzzle - securing devices is equally critical. Personal devices that access business networks can introduce serious vulnerabilities if not properly managed. Without strict controls, BYOD (Bring Your Own Device) policies can create security blind spots.
Using Mobile Device Management (MDM) software is essential for any personal device used to access business applications. MDM allows you to enforce encryption, require passcodes or biometric locks, and remotely wipe business data if a device is lost, stolen, or the employee leaves. Pair this with Multi-Factor Authentication (MFA) on all accounts accessed via personal devices - this simple step can block 99.9% of attacks on user accounts.
Establish clear rules: employees must not download sensitive files to unsecured personal cloud storage or local folders. Require VPNs for any device connecting to the network over public Wi-Fi. And remind staff to never leave devices unattended in public spaces or unlocked vehicles - physical theft remains a real threat.
Quarterly audits are a must. Review which personal devices have access to your network and immediately revoke access for former employees or contractors.
Employee Termination and Access Revocation Procedures
Securing your network doesn’t stop at training and device management. When employees leave, failing to revoke their access promptly can create a major vulnerability. Cybercriminals often monitor platforms like LinkedIn to identify recently terminated employees and exploit their still-active accounts. With attackers able to move laterally within just 62 minutes of gaining access, even a short delay in deactivating accounts can have serious consequences.
"Hackers gain access to networks through inactive accounts, often finding them by searching LinkedIn or other social networks to find people who have recently left organizations."
– Teal
To prevent this, coordinate with HR to ensure IT is notified immediately when an employee departs. Disable their accounts across platforms like Microsoft 365, Google Workspace, and internal systems as soon as possible. For accountability, disable accounts initially rather than deleting them, so you can preserve data for audits or handovers.
Don’t stop at email and internal systems. Review access to third-party tools like Dropbox, Slack, and automation platforms like Zapier. Check VPNs, Remote Desktop Protocol (RDP) instances, and Remote Monitoring and Management (RMM) tools. Shared accounts, such as billing@ or admin@, should have their passwords updated immediately. If the employee had physical access to sensitive areas like server rooms, update keycard permissions or change locks.
Regular access audits are just as important as these immediate steps. Periodically review your systems to ensure no former employees or contractors still have lingering access. By combining strong offboarding practices with ongoing training, you can significantly reduce your risk of a breach.
Prioritizing and Addressing Vulnerability Findings
Risk Prioritization Framework
Spotting vulnerabilities is just the beginning; the real challenge lies in prioritizing which ones to tackle first. With 28.3% of critical vulnerabilities being exploited within just 24 hours of public disclosure, it’s clear that not all issues can be treated equally.
To prioritize effectively, consider these factors: the level of exposure (e.g., systems accessible from the internet), whether the vulnerability is actively being exploited (using resources like CISA's KEV catalog), the potential business impact, and how easily the issue can be resolved.
"The 24-hour exploitation window is no longer the exception - it's becoming the rule." – IBM's X-Force Threat Intelligence Index 2025
Here’s a simple way to categorize vulnerabilities:
- High-risk: Examples include exposed RDP ports, shared admin credentials, lack of backups, or active zero-day exploits. These demand immediate attention - aim to fix them within 24 hours.
- Medium-risk: Issues like unused accounts, weak MFA coverage, or outdated internal software should be addressed within one to two weeks.
- Low-risk: Minor concerns, such as unused SaaS tools or small logging gaps, can be handled during routine maintenance.
After categorizing, focus on creating a clear, actionable plan to address each vulnerability.
Remediation Action Plan
Finding vulnerabilities doesn’t reduce risk on its own; you need a structured plan to address them. Start by assigning ownership - every vulnerability should have a clear point person, whether it’s IT for technical fixes, HR for access management, or Finance for vendor-related issues. Set deadlines based on the risk level, ensuring critical problems are resolved immediately, while others follow a scheduled timeline. Evaluate what resources are needed, whether it’s additional budget for tools or time for testing.
Use a risk-tracking system to stay organized. Document each vulnerability with details like the assigned owner, fix strategy, deadline, and current status. This ensures accountability and aligns with your broader due diligence efforts.
To strengthen your defenses, implement layered controls. For example, combine firewalls, MFA, and regular patching. Address weak remote access by pairing MFA with VPNs or adopting Zero Trust Network Access.
"Discovery alone doesn't reduce risk. You need a structured way to rate vulnerabilities, assign accountability, and track fixes over time." – CitySource Solutions
Once responsibilities are assigned, automate routine fixes to keep up the pace. Automated patch management tools can handle updates for common platforms like Windows, browsers, and CMS systems. Reserve manual efforts for urgent, high-risk vulnerabilities that require immediate attention.
Post-Remediation Validation and Monitoring
Fixing a vulnerability isn’t the end of the road - you need to confirm that the fix actually worked. Test your backups by performing full system restores and ensure they adhere to the 3-2-1 rule.
Follow-up scans are crucial to verify that patches and fixes have been applied correctly. CISA offers free tools like vulnerability and web application scanning through its Cyber Hygiene Services. Additionally, simulated phishing tests can help measure the effectiveness of employee training and identify areas for improvement.
Continuous monitoring is essential. Use 24/7 SOC services, centralized logging, and ongoing patch management to maintain a strong security posture. Regular audits of user accounts, vendor permissions, and cloud configurations ensure that your defenses remain effective over time.
Finally, test your Incident Response Plan with tabletop exercises or simulations at least once a year. Practicing under simulated pressure can reveal gaps and help your team prepare for real-world scenarios, ensuring a smoother response when it matters most.
Conclusion
Key Takeaways for SMB Buyers
When you acquire a business, you’re also taking on its IT systems - and the risks that come with them. Considering that 43% of cyberattacks target small businesses and the average breach costs $3.1 million for organizations with fewer than 500 employees, ignoring IT security during due diligence can lead to serious financial consequences.
Time is critical: 28.3% of vulnerabilities are exploited within just 24 hours, and lateral movement within compromised networks happens in only 62 minutes. Focus on securing key internet-facing systems like VPNs, firewalls, and Content Management Systems (e.g., WordPress), as these are common entry points for attackers. Adding Multi-Factor Authentication (MFA) to critical accounts can reduce compromises by an impressive 99.9%.
Testing your systems isn’t optional. Tools like Google Drive or Dropbox aren’t true backups - ransomware can encrypt local files and immediately sync the encrypted versions to the cloud. Conduct regular restoration drills to ensure your backups work and audit third-party access quarterly to prevent "API sprawl", which can open doors to supply chain attacks.
Don’t underestimate the human factor. With 85% of breaches involving human error, employee training is as crucial as technical defenses. Make sure you have a clear, actionable Incident Response Plan that includes decision trees and key contacts. As CISA wisely points out:
A simple, documented process that's followed consistently beats a perfect process that exists only on paper.
These insights highlight why a thorough IT assessment is essential - and why Clearly Acquired is designed to simplify this process for SMB buyers.
How Clearly Acquired Supports SMB IT Assessments
Clearly Acquired's AI-powered platform is built to help buyers pinpoint and address IT vulnerabilities before they turn into costly problems. By combining financial analysis and risk screening, the platform evaluates both technical infrastructure and financial performance. It flags security gaps during due diligence, using secure data rooms and automated NDAs to protect confidentiality throughout the process.
We also connect buyers to financing solutions - including SBA 7(a) and 504 loans, as well as conventional options, - that can factor in post-acquisition remediation costs for uncovered vulnerabilities. Beyond that, our team provides ongoing advisory support, helping buyers collaborate with IT specialists, cybersecurity consultants, and compliance experts to confirm findings and prioritize fixes. By merging technology, expert advice, and funding, Clearly Acquired ensures that IT assessments don’t delay deals - they make them stronger.
FAQs
What are the top IT vulnerabilities to address first when acquiring a small or medium-sized business?
The most pressing IT vulnerabilities that demand immediate attention include unsecured internet-facing Remote Desktop Protocol (RDP), weak or reused passwords, particularly those lacking multi-factor authentication, and outdated or unpatched software. Another critical issue is the use of shared administrative credentials, which should be secured without delay.
Focusing on these vulnerabilities helps protect businesses from frequent cyber threats and establishes a more resilient IT security framework.
How does employee training help small businesses prevent cyberattacks?
Employee training is one of the most reliable ways to shield small businesses from cyberattacks because it tackles the human weaknesses that hackers often target. Teaching employees how to recognize phishing emails, avoid suspicious links, and understand social engineering tactics can block some of the most common ways attackers gain access. When employees know what to look for, they're less likely to fall victim to scams and more likely to flag potential threats, lowering the overall risk.
Training also reinforces essential security habits, like creating strong, unique passwords, enabling multi-factor authentication, and keeping software updated. These practices make it harder for attackers to exploit weak credentials or outdated systems. Over time, consistent training builds a security-first mindset, where employees naturally treat cybersecurity as part of their everyday work. This shift not only boosts your company's defenses but also makes successful attacks far less likely.
Why aren’t cloud sync tools like Dropbox considered reliable backups?
Cloud sync tools like Dropbox are great for keeping your files accessible across multiple devices, but they aren't built to function as true backup systems. While they offer ease of use, they fall short when it comes to protecting your data. For instance, if a file is accidentally deleted or becomes corrupted, the changes are often synced across all devices, leaving no intact version to recover.
On the other hand, a dedicated backup solution is designed to store multiple versions of your files. This means you can restore data from a specific point in time, offering an extra layer of security. This feature is crucial for protecting your files from accidental deletions, ransomware attacks, or hardware failures.








%20%20Process%2C%20Valuation%20%26%20Legal%20Checklist.png)




















%20in%20a%20%2420M%20Sale..png)
%20vs.%20Conventional%20Loans%20for%20business%20acquisition.png)





















.png)


.png)
.png)





























.png)